A New Era of Asset Security
TYKT Automates tracking of Warranty, Services, Dispatch, Work Orders, Parts, Location History, Receiving, Leases, Renewals, Vendors, Contracts, Rentals and more.


Inventory Asset Audits
Easily track where your inventory spend, loss or high use programs are
Downtime Prevention
TYKT was designed for maximum runtime of the company’s assets and profits
Operations ROI Analysis
TYKT KPI’s and Dashboard driven reporting allows top level management to understand the operational model of your company

About
Asset Security Solutions & Services
TYKT automation solution integrates wireless communications natively in mobile devices with passive RFID, Smart Tag & BarCode technology using TYKTs embedded drivers. For e.g. When asset crosses beyond physical or digital designated boundary consditions, the custom rules are triggered in the TYKT workflow to tag and check to see if the asset is unedr threat. In the next gen, TYKT can dispatch a message to the asset to deactivate, sound an alarm, perform shutdown or alert staff to a potential security loss before to secure and mitigate it.
ROI using TYKT for Work Orders & Security
The typical ROI calculation shows how much an Work Order Automation investment yielded overall. However, if you’re comparing ROI from two or more investments such as procurement vs maintenance, the amount of time it takes to make a given return matters too. Both those insights and other KPI’s are readily available in TYKT.org
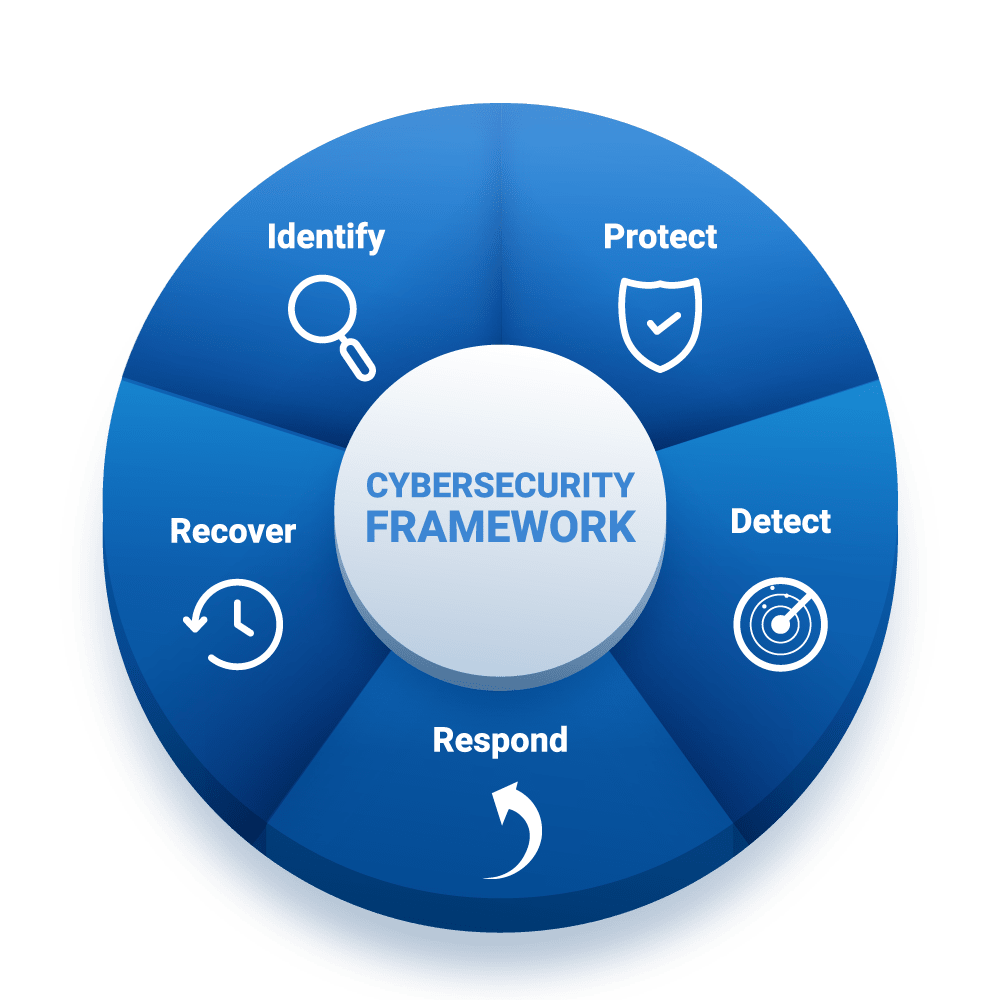
Features
What We Offer
TYKT automation, allows peace of mind solution integrates wireless communications natively in mobile devices with passive RFID, Smart Tag & BarCode technology using TYKTs embedded drivers. For e.g. When asset crosses beyond physical or digital designated boundary consditions, the custom rules are triggered in the TYKT workflow to tag and check to see if the asset is unedr threat. In the next gen, TYKT can dispatch a message to the asset to deactivate, sound an alarm, perform shutdown or alert staff to a potential security loss before to secure and mitigate it.
Security Analysis
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed
Security Services
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed
Security Solutions
Donec sollicitudin molestie malesuada. Vivamus magna justo, lacinia eget consectetur sed

Approach
Our Approach to Asset Inventory Security
TYKT automation solution integrates wireless communications natively in mobile devices with passive RFID, Smart Tag & BarCode technology using TYKTs embedded drivers. For e.g. When asset crosses beyond physical or digital designated boundary consditions, the custom rules are triggered in the TYKT workflow to tag and check to see if the asset is unedr threat. In the next gen, TYKT can dispatch a message to the asset to deactivate, sound an alarm, perform shutdown or alert staff to a potential security loss before to secure and mitigate it.
Security & Complaince
The typical ROI for a Work Order Automation investment yielded both savings and security in automation. However, if you’re investing in Work Orders, Fixs you might as well add security and worker skills matching to the dispatch system two or more investments such as procurement vs maintenance, the amount of time it takes to make a given return matters too. Both those insights and other KPI’s are readily available in TYKT.org
Mauris blandit aliquet
Elit, eget tincidunt nibh pulvinar a. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec velit neque
Contact Us
(246) 000-0000
1234 TYKT St. Coming soon
Monday-Friday: 8am – 5pm
Get Started
Free Demo
